CryptoCTF Wp 2
CryptoCTF WriteUp 2 By huangx607087
0.About
再探CryptoCTF,这里面有些题目难度确实还是比较大的,这几天的解题进度也基本上是一天一题的进度吧,不过确实非常扩展思维的。然而我这么菜的肯定比不上群里那些大佬们。今天的RARCTF还有很多东西没看呢,事情的确多得有亿点点忙不过来了。
好在最近外面疫情严重,自己基本上也就一天待在家里,打CTF,配置Blockbot,摸鱼摸鱼在摸鱼,Hadoop的项目还没测试呢,院科协也有两天没打卡,好在还是补上了。
希望新学期能正常开学,我不想上网课,我只是期末想考61而已。
1.Tuti
1 | |
很显然,这道题告诉你了两段密文之间的关系:$(x^2+1)(y^2+1)-2(x-y)(xy-1)=4(k+xy)$。
第一反应肯定是要把$xy$之类的未知量移到等号一边,然后等号两边展开,自己就什么也看不出来了。
然后我想到了sagemath,这个东西可以分解因数,说不定可以分解因式呢——貌似确实可行,$4xy$移到左边后对左边式子的分解因式结果是$(x+1)^2(y+1)^2$,这确实是一个非常好的结果,很多大佬都是手搓的——然而自己就不行了,因为自己解一元二次方程如果二次项不为$1$自己就分解不出这个式子了(比如$2x^2+7x+3=0$,笔者遇到直接上求根公式——define huangx607087 fw)。
然后对右边直接开平方就是$(x+1)(y+1)$的值了,至于分解右边的那个数字(实测是$14$个因数),根据$x,y$的位数差不多,在加上flag一定是可读字符,直接枚举各种可能性就行了。
1 | |
最后解出来为什么又是丢番图方程,看来CryptoCTF出题人对丢番图情有独钟啊,这让我想起来当年那个科协里的那个对话
1 | |
2.RSAphantine
看名字,很明显,又是跟丢番图有关的
题目就给出了一个方程组,和一个RSA加密的结果
1 | |
第一次乍一看,似乎并没有什么思路,因为三个都是高次方程的组合,三个未知数,确实是求不出来了的。想要消元降次也几乎不可能——因为自己实测过了(
不过这个时候可以把重点聚焦到第一个和第三个式子上,因为第一个式子和第三个式子都有公共的部分就是$2z^5$,并且这两个式子算出来的结果有很长的高位时相同的,这确实是一个令人怀疑的地方——因此,我们可以猜测:对这两个数字除以$2$后直接开五次方,那么就可以得出$z$的准确值。
事实上确实如此,借助python中的iroot直接开根——可以发现这两个数字除以$2$后开五次方根的结果是一样的,而这个数字我们可以认为是解出来的$z$值——事实上解出来确实如此。
解出来之后,$x,y$两个数字就可以很容易地求出来了——我这边用的是$y^6+zy=a_3-2z^5$这个式子通过二分得出结果的,当然也可以用其他的办法求$y$,求出$y$后就可以直接求$x$了,不过最后$x$是负的令我没想到,但assert对了那就说明没问题了。
1 | |
3.Onlude
1 | |
一道矩阵题,加密方法不难,涉及矩阵运算。
题目给出了密文$E$,还有三个辅助量$M_1=LUL,M_2=L^{-1}S^2L,M_{10}=R^{-1}S^8$。 其中$R$是一个随机矩阵,$L,U$是$S$的$LU$分解,即$S=LU$。加密方法为$E=L^{-1}S(A+R)$,$A$就是明文
这边简单地提一下什么是矩阵的$LU$分解,就是对于任意一个矩阵$M$,可以将其沿主对角线拆分成一个上三角矩阵$U$和一个下三角矩阵$L$,使得$LU=S$,其中$\det L=1,\det U=\det S$,因此这种分解方法是唯一的。
由于$M_1=LUL=SL,M_2=L^{-1}S^2L$,根据矩阵的逆运算,因此$M_2^{-1}=L^{-1}S^{-2}L$,因此我们可以有:
$$
M_3=M_1M_2^{-1}=SLL^{-1}S^{-2}L=S^{-1}L=U^{-1}L^{-1}L=U^{-1}
$$
很显然,如果我们想要凑$S$出来,那就要消去$L$,由于我们发现$M_3=S^{-1}L,M_1=SL$,因此我们计算$M_1M_3^{-1}$,有
$$
M_1M_3^{-1}=SLL^{-1}S=S^2
$$
有了$S^2$,那么我们可以计算出$S^8$,进而计算出$S^{-8}$。故
$$
R=(M_{10}(S^{-8}))^{-1}=S^8M_{10}^{-1}
$$
由于$M_3=U^{-1}$,因此对$M_3$直接求逆就得到了$U$。到目前为止,$R,U$都得到了,而$E=L^{-1}S(A+R)=U(A+R)=UA+UR$,因此$A$很容易就可以得到了。然后根据他的规则,将矩阵里对应的数字转化成字典中的内容,这道题就解出来了。
1 | |
4.Triplet
一个远程交互的题目,看起来似乎有点难度,也有点脑洞
1 | |
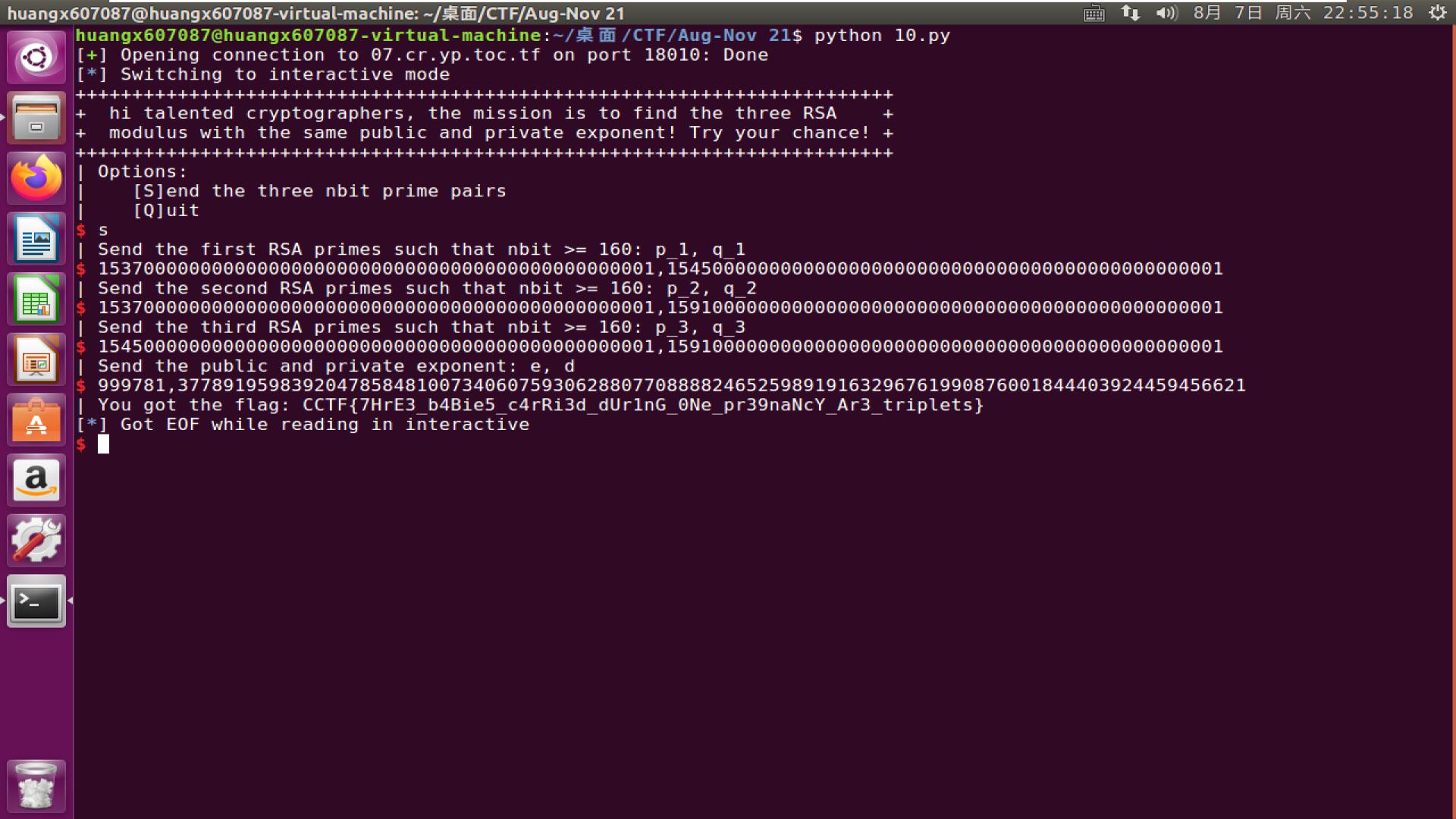
简单看过代码后,就是你要构造三个不同的RSA模数$n_1,n_2,n_3$,大小必须超过$320$位(也就是两个$160$位的素数相乘)。使得这三个模数拥有一组相同的$(e,d)$,使得$(e,d)$均小于三个$\phi$值。简而言之就是要让$ed$的值很小且不能为$1$。
由于$ed\equiv 1 \pmod \phi$。根据扩展中国剩余定理,由于三个$\phi$不同,但$ed$相同,因此这里$ed$除了$1$,只能让$\mathrm{lcm}(\phi_1,\phi_2,\phi_3)$的值足够小。换句话就是让$\gcd(\phi_1,\phi_2,\phi_3)$足够大。
因此,我们可以构造三个素数$p,q,r=k_ig+1$,其中$i$取值为$1$到$3$,$k_i$远小于$g$,而这个$g$,就是我们所想要的$\gcd(\phi_1,\phi_2,\phi_3)$。我们可以构造$g=2^{158},2^{159},2^{160}$,当然这边为了方便起见,我在这里的$g$选择了$10$的次幂,因为这样看起来顺眼(x
于是可以构造: $p=1537000000000000000000000000000000000000000000001$,$q=1545000000000000000000000000000000000000000000001$,$r=1591000000000000000000000000000000000000000000001$
,这样子三个$\phi$的公约数就很大了。然后我们分别对服务器发送$p,q$,$p,r$,$q,r$,完成第一步。
然后我们计算$L=\mathrm{lcm}(\phi_1,\phi_2,\phi_3)$,得:
$$
L=3778092015000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001
$$
分解这个$L$,有
$$
31×32251×3778919598392047858481007340607593062880770888824652598919163296761990876001844403924459456621
$$
因此我们有$e=31×32251=999781$,$d=3778919598392047858481007340607593062880770888824652598919163296761990876001844403924459456621$。直接发送过去就可以得到最后的结果
5.Tiny ECC
1 | |
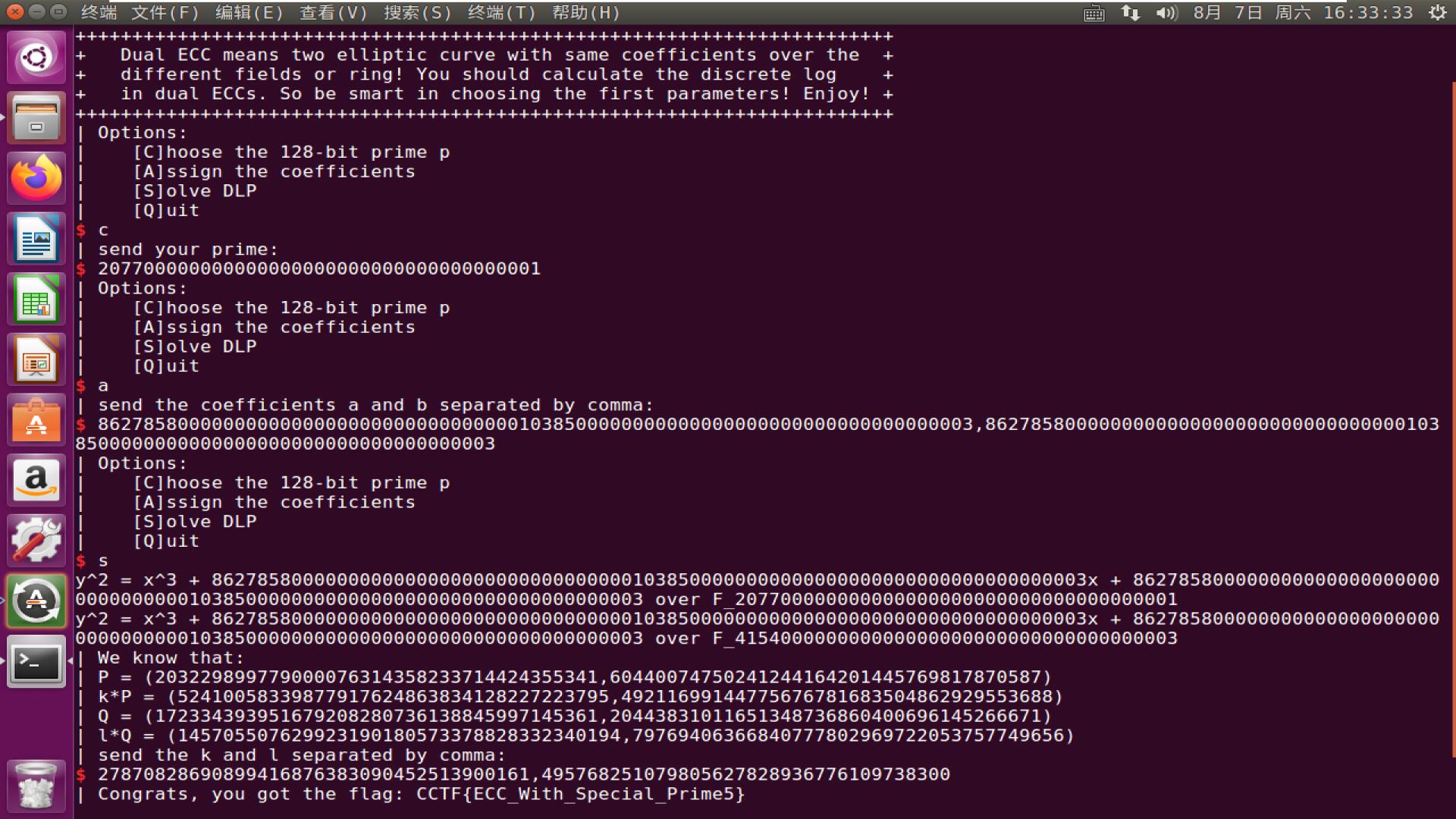
又是一个交互题,题目是发送一个素数$p$,且$q=2p+1$也是素数,并自定椭圆曲线系数$a,b$,最后在$GF(p),GF(q)$上分别解一次椭圆曲线上的离散对数即可获得flag。
很显然,这边就是要构造一个特殊的曲线,这样才能很容易地解出ECDLP。很显然,最简单的椭圆曲线就是$y^2=x^3$,也就是此时$(0,0)$点在椭圆曲线上。
这里我选择了$p=207700000000000000000000000000000000001$,$q=2p+1=415400000000000000000000000000000000003$,符合题目条件。
但题目规定:$a,b$均不能为$0$,但是题目只说了$ab≠0$——很显然,这是一个漏洞,因为它这边没有取模。因此我们只需要计算$n=pq$,然后将$a,b$的值都定为$n$即可,此处有
$$
n=86278580000000000000000000000000000001038500000000000000000000000000000000003
$$
然后我们利用有限域上的极其特殊的椭圆曲线$y^2=x^3$的求解dlp的公式,就可以求出最终的结果了。
这个公式很简单,设$P(x,y),Q=kP$,定$f(P)=\dfrac x y$,那么:
$$
k=\dfrac {f(Q)}{f(P)}
$$
所以最后的解题过程就很简单了
1 | |
最终解题结果:
6.总结
这5道题的思维量明显要比前5题的思维量难度大的,尤其是第4题和第5题,是一种全新的题型,直接就是让你构造特殊的素数和特殊的曲线,并在特殊的条件下求解一些难题——这种出题思维还是很不平常的,长见识了。而第1,2题对数感的要求要非常的好,比如近似数,还有那个分解因式(自己的短板,解二次项不为1的方程直接上公式了)
哦对,顺便提一下我在4,5两题里面构造的这种特殊素数:前面$4$位是随机的,中间一堆$0$,最后一个$1$,这种素数还有一个特点,就是$p-1$极度光滑——因为你除掉所有的$10$因数就还剩几千了,说不定以后会在什么题里遇到。